Port Knocking technique adds an extra layer of security to your server and network, which will make it little harder for intruders to hack the system.
In this article, we’ll explain the following on a very high-level:
- What is a port?
- What are port attacks?
- What is port knocking and how it helps?
Basics of Computer Ports
Computer ports can be of two types :
- Hardware Ports
- Software Ports
A hardware port is a physical slot on a computer through which other devices can be connected to it. Usually port specific wires are used to connect other peripherals to a computer.
On the other hand, a software port is a term given to an end point which a process reserves for communication with processes on same or other computers on network. A port along with the IP address of the computer on network forms a unique identity of an end point in communication. In a communication between a server computer and a client computer, the server socket is identified with it’s combination of IP address and port while client’s socket is identified with combination of it’s IP address and port. Together these IP addresses and ports form a 4-tuple that uniquely identifies a client-server connection.
In the concept of port knocking, the discussion would be centred around software ports.
Port Attacks
In context with the topic of this article, let’s discuss an attack technique (that involves ports) to give you an idea about how ports can be used to launch attacks on computer systems or networks. The attack technique that we will discuss is Port Scanning.
Port Scanning is an attack technique in which attackers scan all the ports of a system on which some application is running. These type of ports (on which some application is running) are also known as open ports. So, to put in another way, attackers try to scan your system for open ports. As we all know that applications listen on ports to communicate with existing and new clients. So, port scanning technique is used to identify ports on which a vulnerable application is running. By vulnerable application, I mean a service that attackers can easily exploit and intrude into the system.
For example, HTTP services run on port 80, FTP services run on port 21 etc. Once such a port is identified then attackers establish a connection on that particular port with the corresponding service and then intrude your system by exploiting a known vulnerability in that service.
On a related note, for anybody dealing with system security, they should understand What is DHCP and How DHCP Works.
Port Knocking
Port knocking is a protection technique that can be used as an extra layer of security over the existing defence systems. The very basis of this technique lies on the fact that only open ports can cause security problems. So, this technique makes sure that none of the port is open initially. Now, one would ask, if there are no ports open then how would communication take place? Well, the answer lies in the capability to secretly knock a combination of fixed ports.
To easily understand it, lets consider a real world scenario where ‘A’ has locked himself inside his own house to escape from his enemy. Now, any guest can arrive at his door at any point of time. He does not want to turn away trusted persons (like friends and family) while at the same time, he also does not want to let his enemy in. So, as a solution, ‘A’ shares a secret knock with his trusted persons. So, whenever a guest arrives, if he/she does the same secret knock on A’s door then he lets him/her in otherwise he never opens the door.
If you try to map the above explained real world scenario with the concept of port knocking then ‘A’ is your computer/network, door is a port, friends and family are trusted users while enemy is the attacker. So, trusted users know a secret knock that they do on a series of ports and as a result, the computer (on which the knock is done) takes some action. In most of the cases, the action is to open a particular port for communication. For an attacker, as he/she does not know the secret port knock, no ports will ever be open for communication.
The following three steps explains on a very high level what will happen during SSH port knocking. Without port knocking concept, server has to keep the SSH port up and running all the times. But, using the port knocking concept, server will open SSH port 22 only when client does series of port knocks that the server can understand.
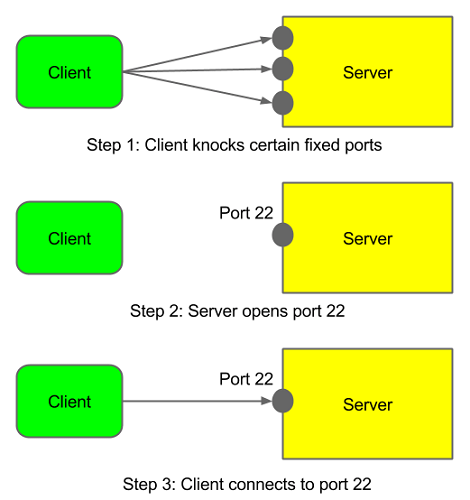
Even if attackers cannot intrude but they will never stop trying. For this, you can configure your firewall in a way that any repeated fail attempts can be logged and appropriate action can be taken against the source from which these attempts are being made.
And even if the attackers try to use brute force attack, the firewall can easily detect and block these connections. Moreover, there are very rare chances that they will succeed because for guessing an unknown combination out of 65535 ports is almost next to impossible.
Advantages and Disadvantages of Port Knocking
Here are some pros and cons of port knocking :
Pros:
- A powerful method to secure a computer system
- Authentication information exchange cannot be hacked easily.
- Can easily be ported to existing applications as not much changes are required.
Cons:
- Cannot be used as an independent security mechanism.
- Client that generates knock should be kept safe.
- A small glitch in this security mechanism can cut off entire system from all it’s clients as ports would always never get opened.
This article provides a very interesting discussion between the creator of port knocking and a major critique of this technique. Though each one is trying to counter argument the other but in the process, the design information and other important stuff that they have discussed is very helpful for a normal reader who is new to this concept.






 My name is Ramesh Natarajan. I will be posting instruction guides, how-to, troubleshooting tips and tricks on Linux, database, hardware, security and web. My focus is to write articles that will either teach you or help you resolve a problem. Read more about
My name is Ramesh Natarajan. I will be posting instruction guides, how-to, troubleshooting tips and tricks on Linux, database, hardware, security and web. My focus is to write articles that will either teach you or help you resolve a problem. Read more about
Comments on this entry are closed.
Excellent one..
Nice article
a very informative article…
Cool thing. Brute force attacks on ssh-service is really annoying. Will there be an article which explains the implementation?
Nice One.
Prectical implementation of the article is just simply use non-default port for wellknown services like ssh,ftp etc. And use /etc/hosts.allow/deny to limit port access based on IP.
Hi,
a very useful and informative article…
thanks..
this is why I love TGS
Excellent article.
Is there a port-knocking-tool for the client?
Do you have an iptables script for the server detecting the correct port knocks?