 Previously we discussed about how to use Nagios to monitor a Linux and Windows server. In this article, let us review how to monitor active sessions and temperature of VPN device using Nagios. You can monitor pretty much anything about a hardware using the nagios check_snmp plug-in.
Previously we discussed about how to use Nagios to monitor a Linux and Windows server. In this article, let us review how to monitor active sessions and temperature of VPN device using Nagios. You can monitor pretty much anything about a hardware using the nagios check_snmp plug-in.
1. Identify a cfg file to define host, hostgroup and services for VPN device
You can either create a new vpn.cfg file or re-use one of the existing .cfg file. In this article, I’ve added the VPN service and hostgroup definition to an existing switch.cfg file. Make sure the switch.cfg line in nagios.cfg file is not commented as shown below.
# grep switch.cfg /usr/local/nagios/etc/nagios.cfg cfg_file=/usr/local/nagios/etc/objects/switch.cfg
2. Add new hostgroup for VPN device in switch.cfg
Add the following ciscovpn hostgroup to the /usr/local/nagios/etc/objects/switch.cfg file.
define hostgroup{
hostgroup_name ciscovpn
alias Cisco VPN Concentrator
}
3. Add new host for VPN device in switch.cfg
In this example, I’ve defined two hosts–one for primary and another for secondary Cisco VPN concentrator in the /usr/local/nagios/etc/objects/switch.cfg file. Change the address directive to your VPN device ip-address accordingly.
define host{
use generic-host
host_name cisco-vpn-primary
alias Cisco VPN Concentrator Primary
address 192.168.1.7
check_command check-host-alive
max_check_attempts 10
notification_interval 120
notification_period 24x7
notification_options d,r
contact_groups admins
hostgroups ciscovpn
}
define host{
use generic-host
host_name cisco-vpn-secondary
alias Cisco VPN Concentrator Secondary
address 192.168.1.9
check_command check-host-alive
max_check_attempts 10
notification_interval 120
notification_period 24x7
notification_options d,r
contact_groups admins
hostgroups ciscovpn
}
4. Add new services to monitor VPN active sessions and temperature in switch.cfg
Add the “Temperature” service and “Active VPN Sessions” service to the /usr/local/nagios/etc/objects/switch.cfg file.
define service{
use generic-service
hostgroup_name ciscovpn
service_description Temperature
is_volatile 0
check_period 24x7
max_check_attempts 4
normal_check_interval 10
retry_check_interval 2
contact_groups admins
notification_interval 960
notification_period 24x7
check_command check_snmp!-l Temperature -o .1.3.6.1.4.1.3076.2.1.2.22.1.29.0,.1.3.6.1.4.1.3076.2.1.2.22.1.33.0 -w 37,:40 -c :40,:45
}
define service{
use generic-service
hostgroup_name ciscovpn
service_description Active VPN Sessions
is_volatile 0
check_period 24x7
max_check_attempts 4
normal_check_interval 5
retry_check_interval 1
contact_groups admins
notification_interval 960
notification_period 24x7
check_command check_snmp!-l ActiveSessions -o 1.3.6.1.4.1.3076.2.1.2.17.1.7.0,1.3.6.1.4.1.3076.2.1.2.17.1.9.0 -w :70,:8 -c :75,:10
}
5. Validate the check_snmp from command line
Check_snmp plug-in uses the ‘snmpget’ command from the NET-SNMP package. Make sure the net-snmp is installed on your system as shown below. If not, download it from NET-SNMP website.
# rpm -qa | grep -i net-snmp net-snmp-libs-5.1.2-11.el4_6.11.2 net-snmp-5.1.2-11.el4_6.11.2 net-snmp-utils-5.1.2-11.EL4.10
Make sure the check_snmp works from command line as shown below.
# /usr/local/nagios/libexec/check_snmp -H 192.168.1.7 \ -P 2c -l Temperature -w :35,:40 -c :40,:45 \ -o .1.3.6.1.4.1.3076.2.1.2.22.1.29.0,.1.3.6.1.4.1.3076.2.1.2.22.1.33.0 Temperature OK - 35 38 | iso.3.6.1.4.1.3076.2.1.2.22.1.29.0=35 iso.3.6.1.4.1.3076.2.1.2.22.1.33.0=38 # /usr/local/nagios/libexec/check_snmp -H 192.168.1.7 \ -P 2c -l ActiveSessions -w :80,:40 -c :100,:50 \ -o 1.3.6.1.4.1.3076.2.1.2.17.1.7.0,1.3.6.1.4.1.3076.2.1.2.17.1.9.0 ActiveSessions CRITICAL - *110* 20 | iso.3.6.1.4.1.3076.2.1.2.17.1.7.0=110 iso.3.6.1.4.1.3076.2.1.2.17.1.9.0=20
In this example, following parameters are passed to the check_snmp:
- -H, –hostname=ADDRESS Host name, IP Address, or unix socket (must be an absolute path)
- -P, –protocol=[1|2c|3] SNMP protocol version
- -l, –label=STRING Prefix label for output from plugin. i.e Temerature or ActiveSessions
- -w, –warning=INTEGER_RANGE(s) Range(s) which will not result in a WARNING status
- -c, –critical=INTEGER_RANGE(s) Range(s) which will not result in a CRITICAL status
- -o, –oid=OID(s) Object identifier(s) or SNMP variables whose value you wish to query. Make sure to refer to the manual of your device to see all the supported and available oid’s for your equipment. If you have more than two oid’s, separate them with comma.
In the ActiveSessions example, two OID’s are getting monitored. i.e one for VPN LAN-2-LAN tunnels (iso.3.6.1.4.1.3076.2.1.2.17.1.7.0) and another for PPTP sessions (iso.3.6.1.4.1.3076.2.1.2.17.1.9.0). In the above example, VPN LAN-2-LAN active sessions has exceeded the critical limit of 100.
Object Identifier (OID) is arranged in a hierarchical Management Information Base (MIB) tree with roots and branches based on the internet standard.
6. Validate configuration and restart nagios
Verify the nagios configuration to make sure there are no warnings and errors.
# /usr/local/nagios/bin/nagios -v /usr/local/nagios/etc/nagios.cfg Total Warnings: 0 Total Errors: 0 Things look okay - No serious problems were detected during the pre-flight check
Restart the nagios server to start monitoring the VPN device.
# /etc/rc.d/init.d/nagios stop Stopping nagios: .done. # /etc/rc.d/init.d/nagios start Starting nagios: done.
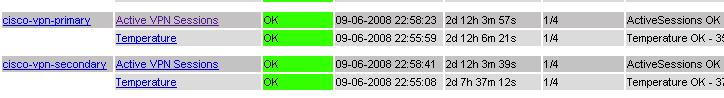
Verify the status of the ActiveSessions and Temperature of the VPN device from the Nagios web UI (http://{nagios-server}/nagios) as shown below.
7. Troubleshooting
Issue: check_snmp works without any issues from Linux command line, but Nagios web UI displays following error:
Status Information: SNMP problem - No data received from host CMD: /usr/bin/snmpget -t 1 -r 5 -m '' -v 1 [authpriv] 192.168.1.7:161
Solution: Make sure the check_command definition for check_snmp plugin in the switch.cfg file is properly defined. The arguments to the check_snmp command should match the check_snmp definition in the /usr/local/nagios/etc/commands.cfg
check_command check_snmp!Temperature!.1.3.6.1.4.1.3076.2.1.2.22.1.29.0,.1.3.6.1.4.1.3076.2.1.2.22.1.33.0!37,:40!:40,:45 [Note: This is wrong, as it is passing 4 arguments to check_snmp command The value after the exclamation is considered as one argument. !{argument1}!{argument2}] check_command check_snmp!-l Temperature -o .1.3.6.1.4.1.3076.2.1.2.22.1.29.0,.1.3.6.1.4.1.3076.2.1.2.22.1.33.0 -w 37,:40 -c :40,:45 [Note: This is correct, as it is passing 1 argument to check_snmp command The value after the exclamation is considered as one argument. !{argument1}]
In the check_snmp command definition shown below, there is only one $ARG1$ argument. So, in the switch.cfg, while defining the check_snmp, you need to pass only one argument as shown above.
# 'check_snmp' command definition
define command{
command_name check_snmp
command_line $USER1$/check_snmp -H $HOSTADDRESS$ $ARG1$
}
Recommended Reading
These are the two best book that covers the latest Nagios 3. I strongly recommend that you read both of these books to gain a detailed understanding on Nagios.
 |
 |






 My name is Ramesh Natarajan. I will be posting instruction guides, how-to, troubleshooting tips and tricks on Linux, database, hardware, security and web. My focus is to write articles that will either teach you or help you resolve a problem. Read more about
My name is Ramesh Natarajan. I will be posting instruction guides, how-to, troubleshooting tips and tricks on Linux, database, hardware, security and web. My focus is to write articles that will either teach you or help you resolve a problem. Read more about
Comments on this entry are closed.
In your snmp commands you don’t have a community name, which implies you are still using the default ‘public’ community name. Admins wanting to poll an snmp device with a name other than ‘public’ will have to insert that parameter. It seems like you’re encouraging people to use low security. Is your excuse that you are monitoring private addresses in these examples?
hello I have a question am possible you nagios3 also uses for two Cisco routers with VPN ipsec?
Kind regards
How to monitor Firewall behind windwos server in nagios