Whenever we come across the term cryptography, the first thing and probably the only thing that comes to our mind is private communication through encryption. There is more to cryptography than just encryption. In this article, we will try to learn the basics of cryptography.
The Basic Principles
1. Encryption
In a simplest form, encryption is to convert the data in some unreadable form. This helps in protecting the privacy while sending the data from sender to receiver. On the receiver side, the data can be decrypted and can be brought back to its original form. The reverse of encryption is called as decryption. The concept of encryption and decryption requires some extra information for encrypting and decrypting the data. This information is known as key. There may be cases when same key can be used for both encryption and decryption while in certain cases, encryption and decryption may require different keys.
2. Authentication
This is another important principle of cryptography. In a layman’s term, authentication ensures that the message was originated from the originator claimed in the message. Now, one may think how to make it possible? Suppose, Alice sends a message to Bob and now Bob wants proof that the message has been indeed sent by Alice. This can be made possible if Alice performs some action on message that Bob knows only Alice can do. Well, this forms the basic fundamental of Authentication.
3. Integrity
Now, one problem that a communication system can face is the loss of integrity of messages being sent from sender to receiver. This means that Cryptography should ensure that the messages that are received by the receiver are not altered anywhere on the communication path. This can be achieved by using the concept of cryptographic hash.
4. Non Repudiation
What happens if Alice sends a message to Bob but denies that she has actually sent the message? Cases like these may happen and cryptography should prevent the originator or sender to act this way. One popular way to achieve this is through the use of digital signatures.
Types of Cryptography
There are three types of cryptography techniques :
- Secret key Cryptography
- Public key cryptography
- Hash Functions
1. Secret Key Cryptography
This type of cryptography technique uses just a single key. The sender applies a key to encrypt a message while the receiver applies the same key to decrypt the message. Since only single key is used so we say that this is a symmetric encryption.
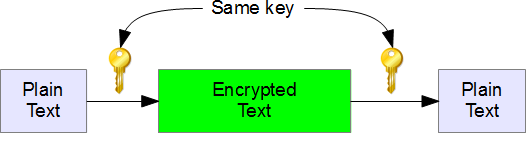
The biggest problem with this technique is the distribution of key as this algorithm makes use of single key for encryption or decryption.
2. Public Key Cryptography
This type of cryptography technique involves two key crypto system in which a secure communication can take place between receiver and sender over insecure communication channel. Since a pair of keys is applied here so this technique is also known as asymmetric encryption.

In this method, each party has a private key and a public key. The private is secret and is not revealed while the public key is shared with all those whom you want to communicate with. If Alice wants to send a message to bob, then Alice will encrypt it with Bob’s public key and Bob can decrypt the message with its private key.
This is what we use when we setup public key authentication in openssh to login from one server to another server in the backend without having to enter the password.
3. Hash Functions

This technique does not involve any key. Rather it uses a fixed length hash value that is computed on the basis of the plain text message. Hash functions are used to check the integrity of the message to ensure that the message has not be altered,compromised or affected by virus.
So we see that how different types of cryptography techniques (described above) are used to implement the basic principles that we discussed earlier. In the future article of this series, we’ll cover more advanced topics on Cryptography.






 My name is Ramesh Natarajan. I will be posting instruction guides, how-to, troubleshooting tips and tricks on Linux, database, hardware, security and web. My focus is to write articles that will either teach you or help you resolve a problem. Read more about
My name is Ramesh Natarajan. I will be posting instruction guides, how-to, troubleshooting tips and tricks on Linux, database, hardware, security and web. My focus is to write articles that will either teach you or help you resolve a problem. Read more about
Comments on this entry are closed.
Perfectly timed article! I just encountered a situation with my daughter who needed to send some private data to an employer and I suddenly realized that “this is a big deal”! It seems to me that this issue should be requisite knowledge for everyone nowadays, and the situation with my daughter was a wake-up call to me that I need to learn this stuff – and fast! So, you have started my journey and I look forward to the next installments. As always, you do a top-notch job and always target relevant material. Many, many thanks!
as usual, excellent job.
Hi,
Very nice article ..
this article is very interesting. but sir i have confusion b/w steganography & cryptography. could u explain it.
nice start… go ahead
Superb article.
As a quick answer to yogesh :
Steganography is nothing but “hiding” data within others data, when cryptography is about making data not readable but still visible.
Cryptography example : In a encrypted VPN you can see data but not understand it…
Steganography example : In a “cat picture” (stored on your computer) you hide your “bank account log and passwd” (do not do this!)…
For more comprehensive entry to cryptography, check this.
Nice – except for one thing.
If you encrypt with a PRIVATE key, then ANYONE with the PUBLIC key can decrypt it. Not a secure method.
You need to encrypt with the recipients PUBLIC key which everyone has, but only the receiver with his PRIVATE key can decrypt.
Your diagram suggests the insecure method.
Simon.
This article is helpfull to anyone use SSH.
@Simon,
Thanks for pointing out the mix-up in the diagram. It is fixed now.
Need of the hour, every one should know about this, linux sysadmins need this when they use python pearl scripts to automate things and where ever they put password it will be in hash ssh format. please include this too
Sir,
Can you please tell me in public key cryptography,how can we enforce that the message encrypted with bob’s public key open can only open with bob’s private key?
Abhishek Joshi
Bob has to send his public key to Alice (for example). Alice will use Bob’s public key to encrypt her messages. When Bob gets Alice’s messages, he will use his private key to decrypt her messages. Remember that Bob only sends out his public key.
This is a nice article. Thanks for the eye-opener.
It is very nice article. i choose this article for my seminar. It is easy to understand
and also for use.
Good article. waiting for sequels. 🙂
Nice one.
A nice and useful article with basic of cryptography thanks a lot
thank you for this article it actually gave a basic idea of what is cryptography and what is it made of!!!!
Hi sir. I wanted to to ask you..what is principle of cryptography flipping coin..did you can explain? I couldn’t understand the topic..tq
hello sir….. yours article is really awesum
thanku 4 ur valuable information
Nice article
Nice
Very useful article….thank you sir.